In this article, we will analyse a real case of a cyber security incident and explore the lessons learned from this event. The case study highlights the importance of taking a proactive approach to cyber security and emphasises the need to implement robust measures to protect data and infrastructure.
Case Study: Ransomware Attack
A medium-sized retail company recently experienced a ransomware attack that paralysed its operations and put its sensitive data at risk. The attack began when an employee opened a phishing email disguised as official communication from a vendor. The email contained a malicious attachment that, when opened, initiated the encryption process of the company’s files.
The ransomware quickly spread through the company’s systems, making the data inaccessible and demanding a ransom in cryptocurrency for its release. The company found itself in a delicate situation, facing the prospect of losing valuable data, business disruption, and potential damage to its reputation.
Response and Recovery:
Faced with this critical situation, the company implemented its cyber security incident response plan, which included the following steps:
- Isolation and containment: The company’s cyber security team acted swiftly to isolate the infection, shutting down the compromised systems and preventing the spread of the ransomware.
- Forensic analysis: Forensic cyber security experts were called in to investigate the attack’s origin, identify the exploited vulnerabilities, and collect evidence for future legal actions.
- Communication and notification: The company immediately communicated the incident to stakeholders, including customers, suppliers, and relevant authorities, in compliance with data breach notification regulations.
- Restoration and recovery: The IT team worked tirelessly to restore the affected systems from recent backups and implement additional security measures to prevent future attacks.

Response & Recovery | Empire Technologies
Cyber Security Recommendations from Empire Technologies to protect your assets and mitigate cyber security risks:
Implement the Essential Eight. This comprehensive cyber security framework, developed by the Australian government, provides a solid foundation for protecting your company against cyber threats.
The Essential Eight consists of eight key mitigations that aim to prevent, detect, and respond to cyber-attacks. These recommended practices include administration restriction, patch application, secure device configuration, application control, regular backups, email filtering, secure internet access, and privileged account management. Implementing the Essential Eight can strengthen your cyber security posture and significantly reduce the risks of attacks like ransomware.
Relying on the support of a specialised cyber security company like Empire Technologies can help businesses implement advanced protection measures and ensure the resilience of their systems.
This case study highlights the fundamental nature of cyber security threats and the importance of being prepared to face them. No business is immune to attacks, but with a proactive approach, adequate training, layered security measures, and the right partnership, companies can strengthen their security posture and minimise the damage caused by cyber security incidents. Protect your business, protect your data, and stay two steps ahead of cybercriminals.
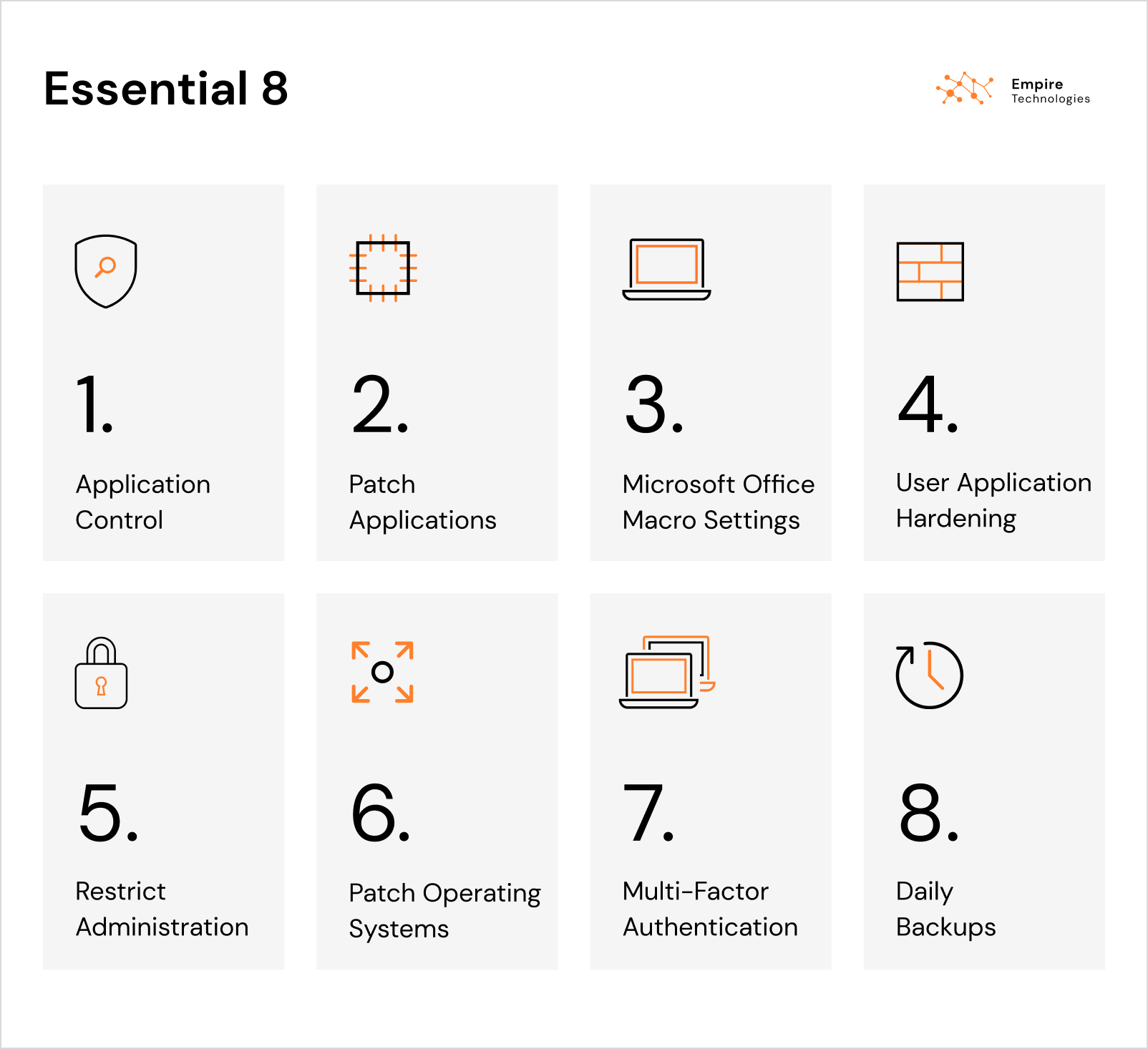
Essential Eight | Empire Technologies
Learn more about Essential Eight in this article: Strengthen Your Cyber Defences with Essential Eight: Stay Informed and Prepared.
Secure your future today!
Connect with us on Instagram and Facebook for more cyber security insights and updates.
Cyber Security