Traditional security measures are no longer sufficient! If your company handles sensitive data, you need to step up to the next level and, at this stage, enter the Zero Trust Architecture – a revolutionary paradigm changing the game of cyber security. This is where the groundbreaking concept of Zero Trust Architecture comes into play.
What is Zero Trust?
Zero Trust represents a paradigm shift in cyber security. Unlike conventional security models that assume trust within an organisation’s network, Zero Trust operates on the foundational principle that trust should never be assumed. It demands continuous verification for every user, device, or system, regardless of its location.
Within the framework of Zero Trust, no user or device is automatically granted trust, even if they are within your organisation’s network perimeter. Instead, access to resources is determined on a case-by-case basis, considering factors such as user identity, device health, location, and context. This approach drastically reduces the attack surface by minimising opportunities for cybercriminals to exploit vulnerabilities.
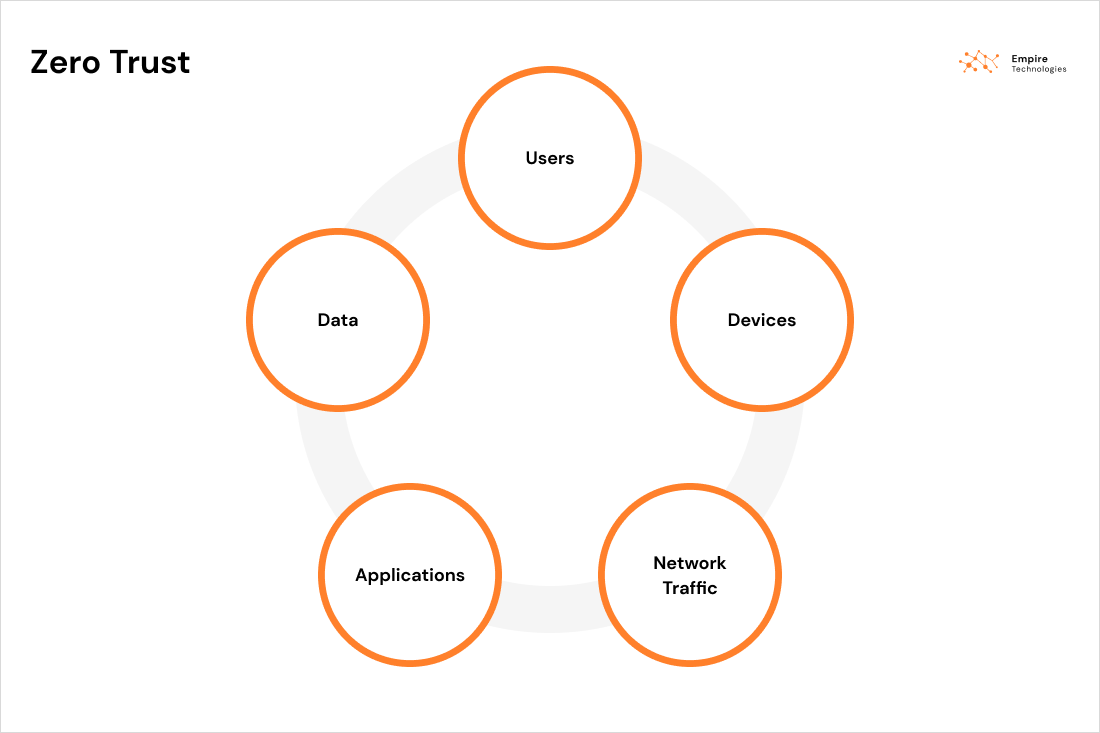
Zero Trust Architecture | Empire Technologies
Why Does Your Company Need Zero Trust?
- Navigating the Evolving Threat Landscape: The landscape of cyber threats is rapidly evolving, rendering traditional perimeter-based security models obsolete. Zero trust proactively examines every access request, effectively reducing your vulnerability to potential breaches.
- Tackling Insider Threats: Internal threats, whether deliberate or inadvertent, pose significant risks. Zero Trust’s meticulous verification ensures that only authorised users can access sensitive data, thereby mitigating the risk of internal breaches.
- Safeguarding Remote Work: As remote work becomes the norm, the traditional concept of network perimeters has dissolved. Zero Trust’s emphasis on identity verification and continuous monitoring is perfectly tailored to secure remote access and cloud environments.
- Preserving Valuable Assets: Critical assets require enhanced protection. Zero Trust guarantees that only authorised personnel can access your most valuable resources, significantly reducing the risk of data leaks or breaches.
- Compliance with Regulatory Standards: In an era of stringent data protection regulations, Zero Trust offers a robust compliance framework. It helps track and manage access to sensitive data, ensuring seamless adherence to regulatory requirements.
- Future-Proofing Your Security: Just as technology evolves, so do threats. Zero Trust’s adaptable approach ensures you’re not only securing for today but also proactively preparing for the challenges of tomorrow.
Implementing Zero Trust: Where to Begin
- Identify Critical Assets: Determine which data and systems require the highest level of protection.
- Micro-Segmentation: Divide your network into smaller segments, ensuring that each segment is accessible only to authorised personnel.
- Multi-Factor Authentication (MFA): Integrate MFA for all access attempts, adding an additional layer of security beyond passwords.
- Continuous Monitoring: Deploy real-time monitoring to identify anomalies and potential breaches promptly.
- Enforcement of Policies: Develop and enforce strict access policies that dictate who can access specific resources.
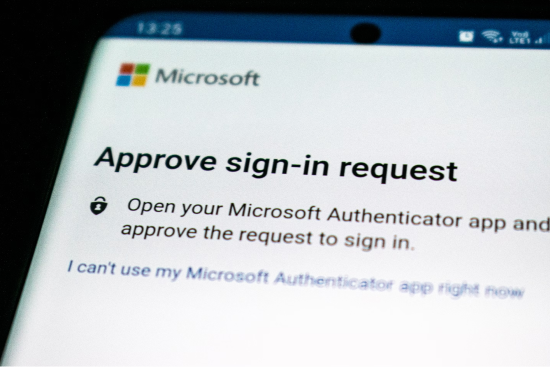
Multi-Factor Authentication (MFA) | Empire Technologies
Zero trust isn’t just a security measure; it’s a strategic approach that safeguards your company’s future. Zero Trust architecture empowers you to navigate the digital landscape confidently with its emphasis on verification, continuous monitoring, and adaptable security. Embrace the future of cyber security, one trust-verified step at a time.
Stay informed, stay cautious, and stay cyber-safe!
Connect with us on Instagram and Facebook, for more cyber security insights and updates.
Cyber Security